
Hunting a criminal network of credit card scams with OSINT
Note: I originally uncovered the titular network in November 2021 when this actor was actively funding targeted social media advertisements. I’m seeking to formalize my investigation here. If I reference a “prior investigation”, I’m talking about my initial discovery on 11/19/21.
Summary
Using publicly available data, I am able to link together over 200 domains that URL hijack storefronts for popular brands. Aside from committing IP infringement, the scammers are collecting payments from unsuspecting social media users and have no intent to deliver the ordered goods.
Identifying the scam
I initially came across this scam the week before Black Friday 2021. A peer of mine lamented that his girlfriend had fallen for a convincing but fraudulent ecommerce site after seeing an ad for sneakers on Facebook. I had some free time, so I asked him to send over the domain in order to take a look. Throughout this post, I will refer to the domain is Domain 1.
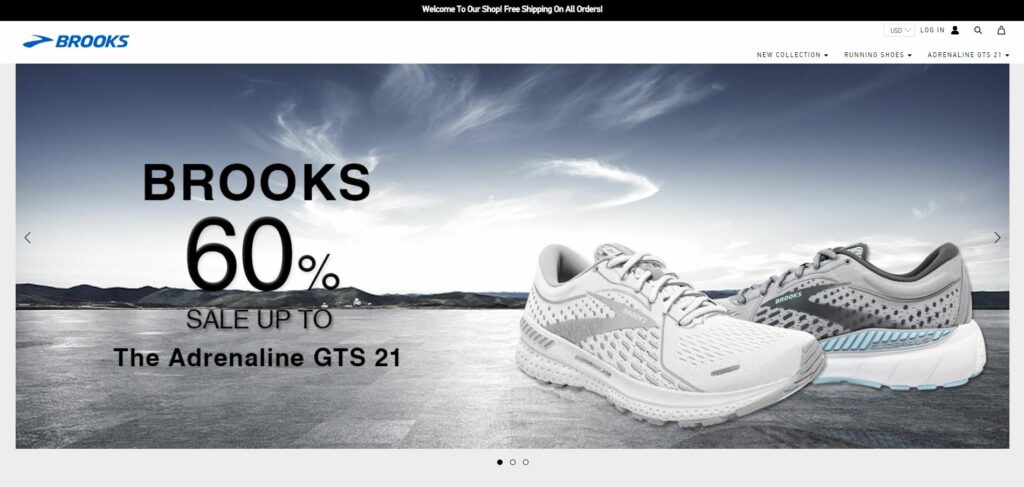
It doesn’t look fantastic, but a casual user could be fooled. Notice the grammatical strangeness on the homepage slider. That’s the first red flag for me.
Plenty of folks rely on the “Padlock” icon in the address bar, otherwise known as a valid TLS/SSL certificate to indicate whether a site is trustworthy or not. While it ensures that there are no third-parties listening in on your HTTPS traffic, it does not ensure that the website to which you’re connected belongs to the organization it claims to. Further, HTTPS only protects your data at the transport layer (after all, TLS = Transport Layer Security); communicating via HTTPS offers no protection against XSS, form jacking, or many other types of attacks.
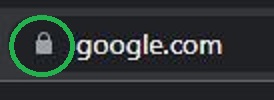
It’s trivial to request and issue a certificate for any domain that you control. Domain 1 has a valid certificate from free CA Let’s Encrypt, but that doesn’t prove the site operator is trustworthy, so we should still be wary.
I always advise anyone who is suspicious of an ecommerce website to check the site footer and contact page. Any reputable organization should have a clear – and real – business address on their website. A site missing that information is trying to avoid revealing their true location.
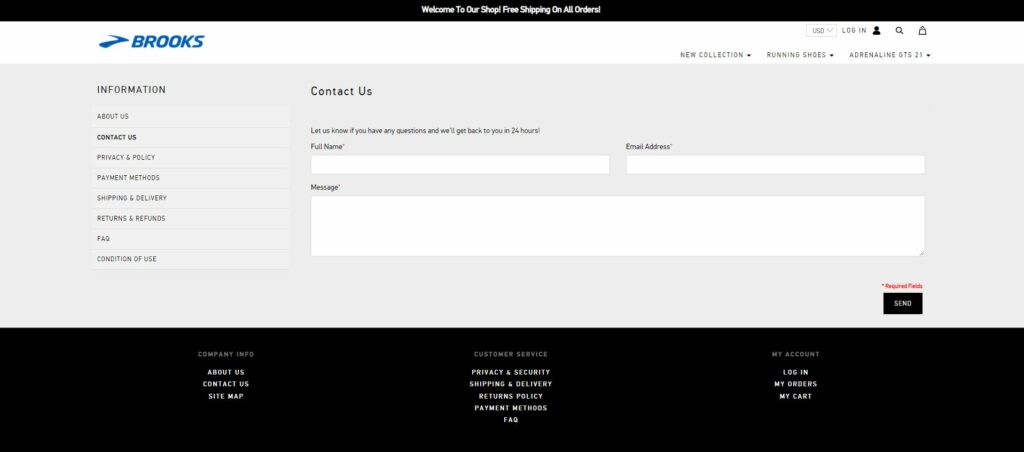
In this case, the site doesn’t have an address, phone number, or email address listed on the contact page, the return policy, the shipping policy, or anywhere else. This is another major red flag. At this point, I’m convinced this is not a trustworthy site. Let’s start digging into OSINT to see who really runs this site.
Whois queries and records
If you’re familiar with Whois, you can skip to the next section.
Every domain in use has to be registered to an individual or organization, called a registrant. The registrant is required to provide contact information, including email address, phone number, and physical address. This information is loaded into what is called a Whois record, which can then be queried from databases accessible to anyone on the Internet.
Typically, I use either the Linux command line program whois or GoDaddy’s Whois tool (if I’m on Windows and the domain uses a common TLD like .com or .net) to look up Whois records. The official Whois portal is hosted by ICANN.
The card-stealing domain uses TLD .us, so I can use the command line tool or whois.us. Either works.
Sometimes, queries may only yield the registrar, nameservers, and registration dates. This is called a thin Whois record. To get the juicy info in a thick record, simply repeat the Whois query at the registrar indicated in the thin record.
You may find that the domain registrant has enabled domain privacy by proxy. In exchange for a small fee, the registrant can pay an organization to use their contact info during domain registration. Privacy limits Whois utility for OSINT investigators that lack subpoena power. Fortunately, privacy was not enabled for our target domain.
Enumerating domains that belong to the first fake identity
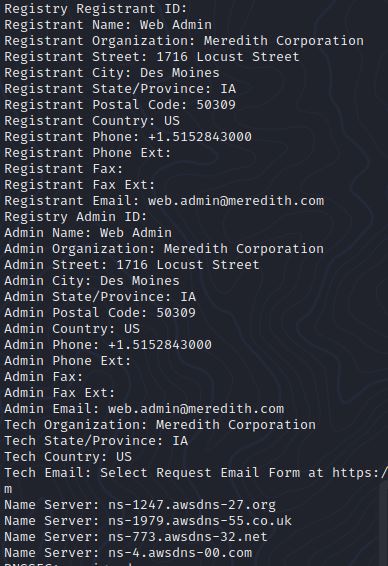
Let’s do a Whois lookup on Domain 1:
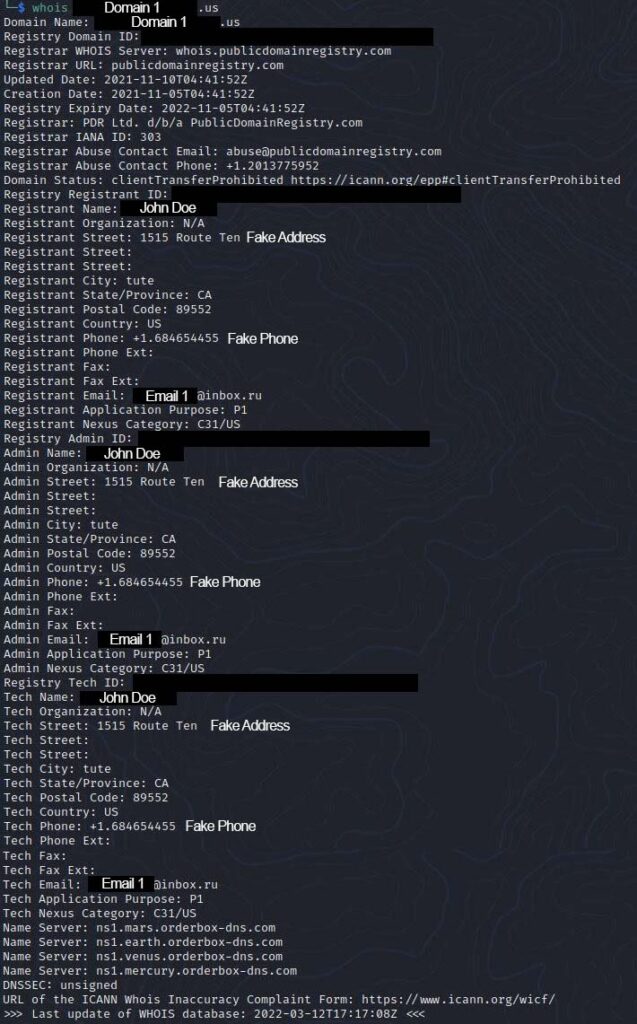
The address and phone number are both fake, but this is a good starting point to do some investigation and analysis. Let’s look at the name and email first.
Name: John Doe
The name provided seems fairly uncommon. I ran it through a list of People Search Engines assembled by the OSINT Framework without any results. I’m confident that it’s a made up name.
Google searching for “john doe tute ca” doesn’t provide any insight as to his identity, but it does provide a few results with complaints about four more domains that have the same Whois registrant. I will call them Domains 2, 3, 4, and 5. I briefly examined each of them.
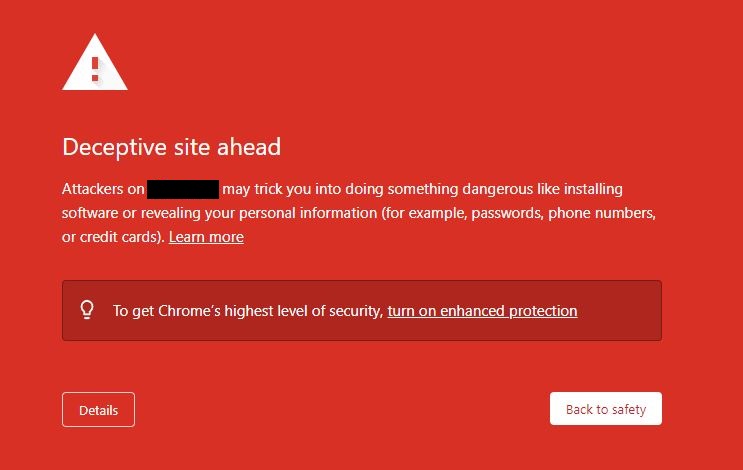
- Domain 2: A slight misspelling of a popular brand of wallet. The site is still live, but my browser very clearly indicates that the website is dangerous.
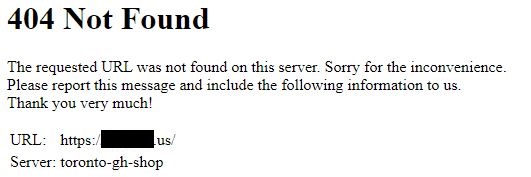
- Domain 3: 404 not found, served by web server Tengine, the web server created by Chinese ecommerce giant Alibaba. The page offers what may be a clue in the future:
- Domain 4: Another misspelling of a brand of shoes. Does not have any DNS records. Nothing stands out.
- Domain 5: Another brand of shoes. During my initial investigation in November, this domain had a site that listed those shoes for sale. I located legal documents from the actual IP holder published in January complaining that this domain was not legitimate. It was shut down via court order.
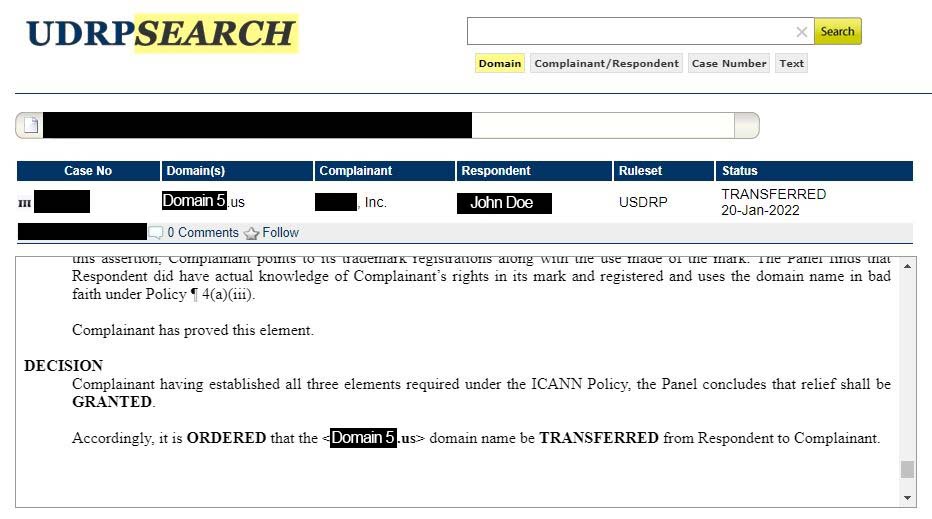
Notable are Domains 2 and 5 – we now have proof that the registrant owns more than one domain conducting nefarious operations. Domain 1 was not a one-off, it’s part of a network.
Email: email1@inbox.ru
The email address is comprised of a first initial and Russian last name. It’s hosted at inbox.ru, a free email provider. Running the address through emailrep.io indicates the address is clearly suspicious.
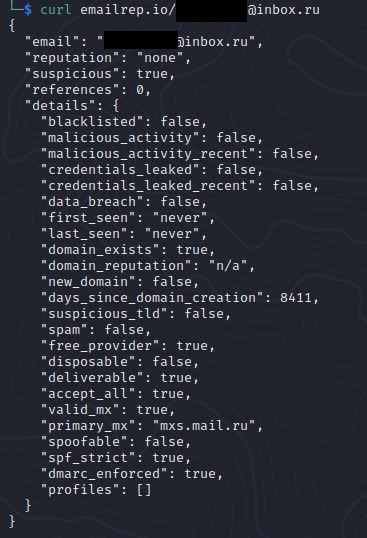
The suspicious flag comes from the fact that the email is from a free provider, has never been seen before, and isn’t associated with any profiles on major sites like Facebook and LinkedIn.
Google searching for the address reveals another three domains with the same registrant, dubbed Domains 6, 7, and 8.
- Domain 6: An AirPods impersonation that is still live.
- Domain 7: No DNS records, very similar to domain 4. Misspelling of Canada Goose Outerwear.
- Domain 8: Same as Domains 4 and 7. Impersonating Allbirds shoes.
Reverse Whois
I’ve completed a Whois search to reveal John Doe’s information, but what if I could search for John Doe’s name or email to find all the domains he owns? It’s possible using a reverse Whois search. I’m using reversewhois.io. With that ability, I was able to locate 26 domains with John Doe’s details on them. Some of them were live in November but have been shut down. Others have been redirected to a 404 page, likely to disguise the site until another high volume shopping holiday like Black Friday. Even more are still live.
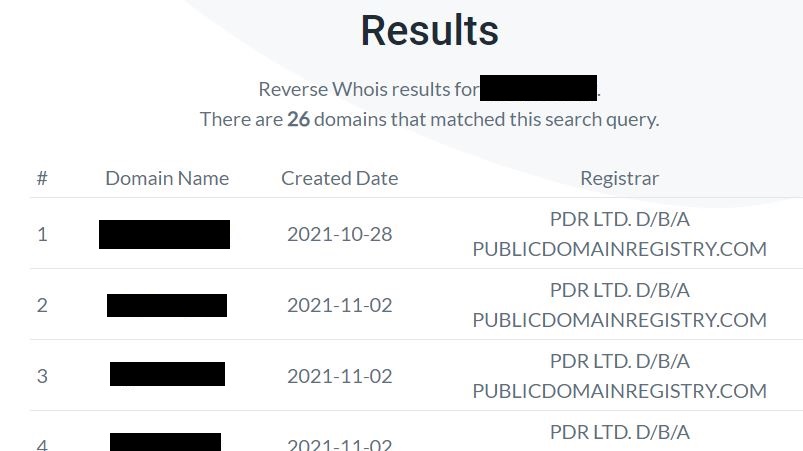
Four of the 26 domains I’ve already discovered, giving us 22 new domains registered to the inbox.ru email address. Almost all of them are typosquatting well-known brands of apparel and consumer goods. I’ll call them Domains 9-30.
Sometimes it can help to reverse Whois search on a couple websites, as the data can sometimes be incomplete. I used Whoxy to find four more domains, Domains 31-34.
Fun with TLDs
I ran an anti-phishing tool called dnstwist to find variations of some of the domains I’ve already identified. Everything I have so far uses the .us ccTLD, but through the script, I found that a good chunk of domains on the list have equivalent domain names with a .com TLD. For instance, domain33.us can be amended to domain33.com to identify another domain with a similar scheme.
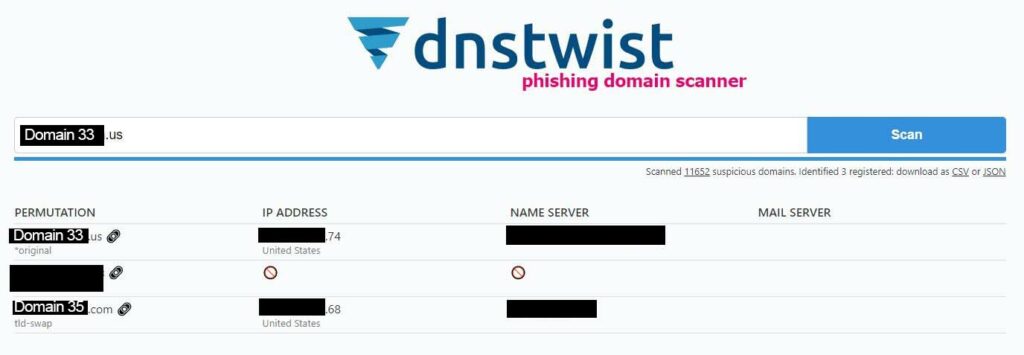
I tried each domain I already had and found 20 of them also used .com. I’ll call the newly identified domains Domains 35 – 54. These sites utilize the same software, have the same copy, and impersonate the same brands. Very notably, they use different nameservers, different DNS records, and different Whois records than those registered to John Doe.
.com Whois records
The Whois records for the .com domains don’t provide much information worth investigating, though they may provide some clues as to the location of the criminals. Of the twenty .com domains I found, nineteen of them were registered in Kuala Lumpur with Alibaba Cloud, the Chinese analogue to AWS. Domain 39 was registered in Hainan, China with Cloud Yuqu LLC, another Chinese registrar. All twenty use domain privacy, so it’s not possible to see any more details about the registrant.
Careful inspection reveals a careless mistake
After careful inspection of each website, I noticed a small clue with big implications on the sites at Domains 11, 12, 22, 33, 35, and 48. Each Contact Us page includes an email address above the form.
Excluding a duplicate, I’ve identified 5 email addresses to explore. One is a Gmail using an English first and last name combination, while the others are generic “sale@” addresses hosted at a seemingly random four letter domain, followed by one of two uncommon TLDs: .online or .vip. I am labelling these emails as Emails 2-6.
It seems that the site operators have used these emails on other websites too. The contact page has been indexed by Google in many cases. By searching for each email, I am able to tack on a lot more domains:
- Email 2: Domain 55
- Email 3: Domains 56 – 69
- Email 4: Domains 70 – 211
- Email 5: None
- Email 6: None
Up to 211 domains now. Checking Whois records and contact form recipients yields another 24 email addresses to investigate; 19 from Whois and 5 from front-end forms. At this point, the work to investigate each email becomes tedious for a few reasons:
- I don’t have API access to programmatically run reverse Whois searches for each email address.
- I’m being rate limited by domain registrar Whois servers, eliminating the possibility for automation and significantly slowing manual queries.
Due to these limitations, I decided to stop looking for new domains. There are undoubtedly more in this network.
To visualize what I’ve uncovered so far, here’s a map I created using Obsidian, my favorite note-taking app.
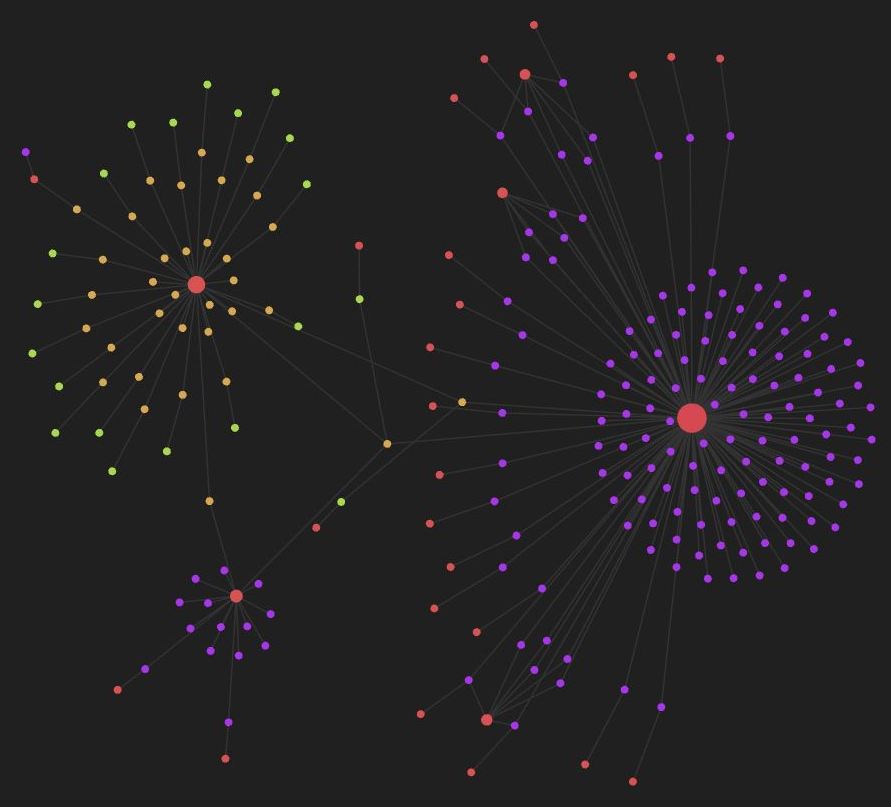
How are these sites attracting and fooling visitors?
The short answer is that the scam is being propagated via social media ads. Not only did I find the first site because someone I know was lured in with a Facebook ad, but inspecting the <head> element in the HTML of each site reveals a tracking pixel.
These pixels opaquely link back to advertising accounts with primarily Facebook and Snapchat. Both services have easily trickable, automated ad account verification. Before banning them, each platform relies on platform users to report scam ads after they’ve had a chance to circulate in the wild.
This behavior creates a brief window between ad creation and account termination wherein scammers maximize their investment by adopting tactics to generate as many “sales” as possible per site before the associated ads account is banned. Such tactics include:
- Adopting the identity of a popular name brand known for high price items and infrequent discounts
- Heavily discounting those products to entice thrifty customers with an interest in those products
- Providing a cover for the discounts by running ads around holidays or popular sales days such as Black Friday
- Unpublishing ads and temporarily decommissioning websites shortly after a sales period as not to attract too many reports, dodging an account ban and prolonging the life of the account
- This was the reason behind the 404 error when visiting Domain 3 and many of the other uncovered domains
- This also serves a dual-purpose; customers who fell for the scam can’t make their way back to the site that scammed them because it’s not up anymore
Who is doing this?
The cybercriminals behind this scam have hidden their tracks well. They’ve employed fake identities, hide behind domain privacy, and use services like Cloudflare’s free tier to roil investigations such as this one. As such, it’s impossible to name an individual or group of individuals responsible.
Further, I can’t say whether those involved are part of the same organization; it’s possible that multiple criminal organizations are working together, similar to how some criminal affiliates license malware from ransomware-as-a-service provider REvil.
What I can confidently say, however, is that the scammers are most likely based in China. I base this conclusion off of several findings:
- The use of the Tengine web server. Tengine was developed by Chinese ecommerce giant Alibaba. While not incriminating by itself, it’s very rare to see Tengine used outside of Asia.
- Some domains without Whois privacy are hosted at a small web host in Guangzhou, China.
- By appending /admin to the URL of each domain, I found that some sites are set to be administered in Mandarin.
While this is far from proof, these observations demonstrate that the scammers have a good understanding of Chinese internet infrastructure and language.